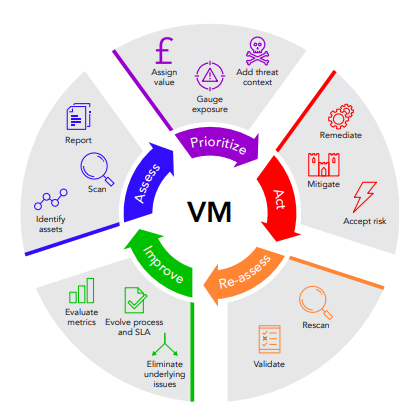
Vulnerability Management
CBDubai offers outstanding solutions to assess potential cybersecurity risks and vulnerabilities to help your business stay competitive and remain secure. CBDubai provides organizations with guidance on how to strengthen the security of their software products, create secure software development workflows, and provide security throughout the development and deployment of software products and services.
Our services enable organizations to defend themselves against cyber attacks and other digital threats to safeguard sensitive information, prevent unauthorized access, reduce risk, and build cyber resilience.
CBDubai provides top-notch cybersecurity services through a variety of pipelines. Our wide range of services ensures that your teams have everything they need to defend your business from online threats and attacks. Our on-demand cybersecurity services include Penetration Testing and Vulnerability Assessment.
PENETRATION TESTING
Can an adversary forcibly gain access to your sensitive information and critical assets? Let us investigate it for you. CBDubai’s Cybersecurity Consulting offers Penetration Testing as a Service (PTaaS).
For continuous testing, reporting, and correction, CBDubai integrates penetration testing into your SDLC. To shorten the “time to fix” in your agile SDLC environment, CBDubai immediately notifies you of security flaws as they are discovered. The PTaaS model is superior, particularly for companies that like to add dynamic digital content as part of their agile releases. In order to evaluate the deterrence potential of an organization’s policies, processes, and technology, Penetration Testing simulates adversary attacks on the IT infrastructure, web applications, Wi-Fi, mobile, and cloud environments.
Mobile & Wi-Fi Penetration Testing
Web Application Penetration Testing
Internal & External Penetration Testing
Thick Client Penetration Testing
Desktop applications, also referred to as thick client applications, are connected to a network, with the client side performing the majority of the processing. Attack surface analysis, data gathering, traffic analysis, reverse engineering, memory & storage analysis, privilege escalation, process injection, and buffer overflow checks are all included in the assessment of thick client applications.
VULNERABILITY ASSESSMENT
Vulnerability assessments are a critical part of IT security, as they uncover security flaws within infrastructure and networks by leveraging vulnerability scanning tools. CBDubai provides clear, actionable reports on all identified issues to help clients remediate the vulnerabilities found during the vulnerability assessment.